Bis zum 39C3 öffne ich täglich ein Türchen zu den langweiligsten Datenlecks der letzten Jahre. Es geht um .git, .env, exponierte dev-Umgebungen und andere technisch langweilige Ursachen. Aber manchmal ist interessant, was sich hinter einem Türchen verbirgt. Alle Türchen sind hier zu finden.
Team Cymru ist ein Unternehmen, das das Internet überwacht. Ihr Gründer und ehemaliger CEO Rabbi Rob Thomas war Mitglied des Tor Boards. Mit dem Nimbus Threat Monitor stellt Team Cymru Informationen zur Threat Detection gratis zur Verfügung, im Tausch gegen Netflow-Daten.
Share your network metadata, and in return, gain access to unparalleled threat detection, free of charge. (Team Cymru Nimbus Threat Monitor)
Wenn ISPs Netflow-Daten sammeln, dann ist das problematisch. Die Daten zeigen, wer mit wem, wann und wie viel kommuniziert hat. Sie umfassen Quell-/Ziel-IPs, Ports, Protokolle, übertragene Bytes und Pakete.
Wenn Team Cymru Netflow-Daten verschiedener ISPs zusammenführt, dann ist das noch problematischer. Zunächst haben die Nutzer*innen einer Übermittlung und Speicherung dieser sensiblen Daten wahrscheinlich nicht zugestimmt. Und dann können diese Daten genutzt werden, um per Traffic-Analyse Nutzer*innen von Anonymisierungsdiensten zu deanonymisieren.
Bei Team Cymru waren Elasticsearch-Instanzen unter etwa 70 verschiedenen IP-Adressen exponiert, überwiegend bei DigitalOcean.
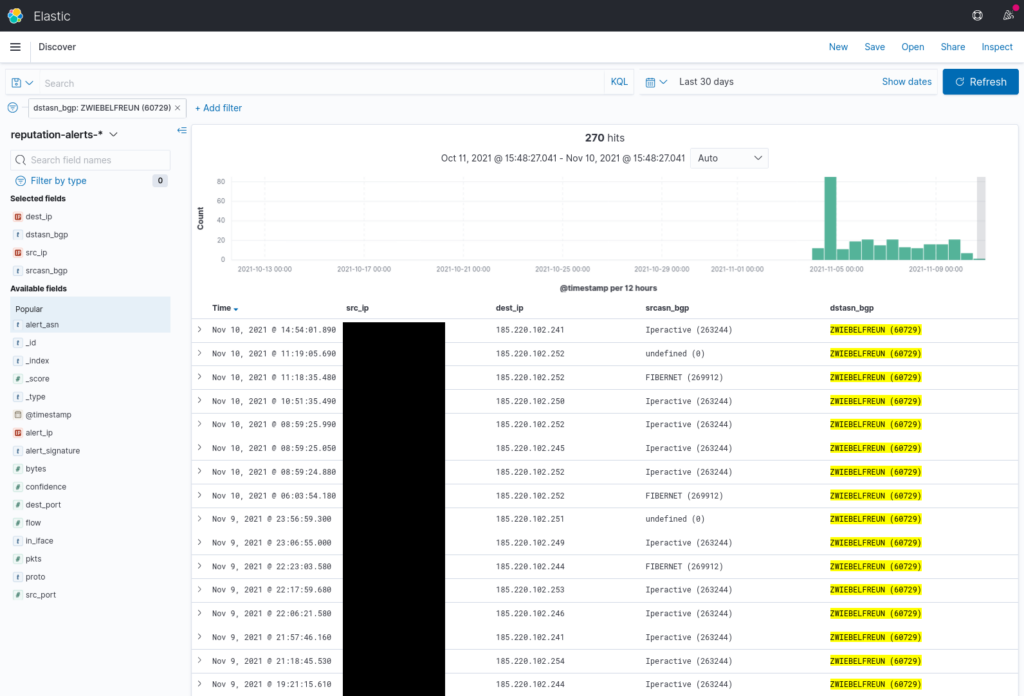
Ich sah nur einen kleinen Ausschnitt der geleakten Daten mit den folgenden Quellen: Iperactive (263244), FIBERNET (269912), BDCONNECTNET-AS-AP (64063), VIJIJI-CONNECT-LIMITED (328856), Messagelabs-AS (328301), Syokinet-Solutions-AS (328271), PREPA-NETWORKS-LLC (23550), HRCOM (46962), IMINTERNET (398326).
2022 hat das Tor Project beschlossen, nicht länger auf von Team Cymru gespendete Infrastruktur zu vertrauen. Im gleichen Jahr hat Rob Thomas das Tor Board verlassen.
Offene Fragen: Welche Rolle spielt Team Cymru bei der Deanonymisierung von Tor-Nutzer*innen? Welche ISPs sammeln und teilen Netflow-Daten?