Nach einem größeren Stromausfall in Berlin plant die Stadt offenbar nicht, die Infrastruktur resilienter zu gestalten oder künftige Reparaturen zu beschleunigen. Stattdessen setzt sie auf den Ausbau von Videoüberwachung mit KI. Die KI soll künftig Veränderungen wie Hitzeentwicklung erkennen.
Parkraumüberwachung in Hamburg
Wie schon Heidelberg und Berlin wird Hamburg Kamera-Fahrzeuge einsetzen, um Kennzeichen geparkter Fahrzeuge mit einer zentralen Datenbank abzugleichen.
Anjes Tjarks meint, dass der Datenschutz vollständig gewährleistet sei. Auch der Datenschutzbeauftragte hatte keine Einwände. Das vergleichbare Projekt in Berlin wurde 2025 wegen fehlender Rechtsgrundlage vorerst auf Eis gelegt.
- Protokoll des Ausschusses für Digitalisierung und Datenschutz mit Präsentation
- Gesetz zum digitalen Parkraummanagement
Behördendomains
Um Transparenz zu fördern, veröffentlichen FragDenStaat und Tim Philipp Schäfers mehr als 2.000 Behörden-Domains. Rene und ich ergänzen diese Liste um weitere 50.000 Domains und Subdomains, einschließlich über 100 zur Zeit nicht registrierter Domains. 20 Domains, beispielsweise bundescriminalamt.de, wurden heute registriert. Die Domains stammen aus diversen Quellen und waren oder sind dem Bund zuzuordnen.
adele-esf.de
altersvorsorgemachtschule.de
arb-5.de
arbeitenbis67.de
ba-reform.de
bildungspaket-bmas.de
bitvlotse.de
briefing4pilot.de
bundescriminalamt.de
bundestag-magazin.de
bundestag-online.de
bundestag-und-schule.de
xn--einsatzfrarbeit-6vb.de
inqa-bestellservice.de
jugendinarbeit.de
ombudsrad.de
vereintaktiv.de
w3-indikatoren.de
wiewerdenwirarbeiten.de
zehnte-ddr-volkskammer.de
60jahresozialstaat.de
xn--allianz-fr-arbeitskrfte-f8b20d.de
xn--allianz-fr-fachkrfte-rzb33c.de
allianz-fuer-arbeitskraefte.de
allianz-fuer-fachkraefte.de
altersvorsorgemachtschule.com
altersvorsorgemachtschule.net
altersvorsorgemachtschule.org
arbeit-4-null.de
arbeit-4-punkt-null.de
arbeiten-4-0.de
arbeiten4null.de
arbeiten4punktnull.de
arbeitenvierpunktnull.de
arbeit-psyche.de
arbeitvierpunktnull.de
ausbildungsportal.org
beschaeftigtebeteiligen.de
beschaeftigung-aelterer.de
xn--beschftigtebeteiligen-91b.de
xn--beschftigung-gestalten-44b.de
bmas-alleinerziehende.de
briefing4aviation.com
briefing4aviation.de
briefing4pilot.com
bspc2007.de
chancen-mit-erfahrung.de
csringermany.de
csrmadeingermany.de
das-bildungspaket.de
das-jobcenter.de
das-rentenreformpaket.de
deutschland-wird-inklusiv.de
einsatzfuerarbeit.de
eparlament.de
e-parliament.de
esf-foerderung.de
esf-programm.de
fachkraefte-allianz.de
xn--fachkrfte-allianz-vqb.de
xn--fachkrftewoche-bib.de
fondsheimkinder.de
fons-civitatis.de
xn--freinlebenswertesland-8hc.de
fuereinlebenswertesland.de
generationenarbeit.de
glasklar-bundestag.de
gp-habitat.de
gph-habitat.de
gute-arbeit-alleinerziehende.de
heimkinder-fonds.de
xn--initiative-fr-fachkraefte-qwc.de
xn--initiative-fr-fachkrfte-f8b50d.de
inqa-check.de
inqa-ddn.de
inqa-demografie.de
inqa-demographie.de
inqa-demographie-netzwerk.de
inqa-epoxibewertung.de
inqa-kmu.de
inqa-mittelstand.de
inqa-produktion.de
inqa-stress.de
job3punkt0.de
jobcenterservice.de
jobcentersuche.de
job-drei-null.de
jobdreipunktnull.de
jobsohnebarrieren.de
lebenslagen-in-deutschland.de
meinmicrocredit.com
meinmicrokredit.org
meinmikrocredit.com
meinmikrocredit.de
met4aviation.com
met4aviation.de
met4pilot.com
met4pilot.de
mindestlohn-gilt.de
mindestlohn-kommt.de
mindestlohn-wirkt.de
mitmischen.tv
mitneuemmut.de
monitoring-esf.de
netzwerk-alleinerziehende.de
neuekulturderarbeit.de
neues-jobcenter.de
ohnedichkeinwir.de
ombudsrat.net
ombudsrat.org
ostseeparlamentarierkonferenz2007.de
parlaments-profi.de
projekt-e-demokratie.de
projekt-persoenliches-budget.de
rentenreformpaket.de
selberhandeln.de
sgb2.com
sgb2-kennzahlen.de
sgb2.net
sgb2.org
sgb2-reform.de
sgbii.com
sgbii-kennzahlen.de
sgbii.net
sgbii.org
sgbzwei.com
sgbzwei.de
sgbzwei.net
sgbzwei.org
sozialpolitische-informationen.de
sozialwahl2011.de
the-unseen.org
uniohneabi.de
un-koordinierungsstelle.de
xn--vereint-fr-gemeinsame-bildung-tbd.de
xn--vereint-fr-gleiche-bildung-6zc.de
vereint-fuer-gemeinsame-bildung.de
vereint-fuer-gleiche-bildung.de
w3-wohlstandsindikatoren.de
was-ist-gute-arbeit.de
wdrei-indikatoren.de
wdrei-wohlstandsindikatoren.de
whochdrei-indikatoren.de
whochdrei-wohlstandsindikatoren.de
wiewollenwirarbeiten.de
yesweareopen.de
Leakvent 26: Fazit und Ausblick
Bis zum 39C3 öffne ich täglich ein Türchen zu den langweiligsten Datenlecks der letzten Jahre. Es geht um .git, .env, exponierte dev-Umgebungen und andere technisch langweilige Ursachen. Aber manchmal ist interessant, was sich hinter einem Türchen verbirgt. Alle Türchen sind hier zu finden.
Das waren 25 Tage mit technisch langweiligen Datenlecks. Keine 0days, keine ausgefeilten Angriffe, nur versehentlich veröffentlichte Ordner, Dateien und Debug-Schnittstellen. Die Folgen dieser groben Schnitzer sind trotzdem bemerkenswert: Parteien, Unternehmen, Gerichte und Behörden verloren Daten oder gaben Zugänge zu internen Portalen frei.
Ein Highlight waren Lycamobile und Variatel, die genau wie Numa zeigen, dass das Hochladen von Ausweis-Fotos keine gute Idee ist. Aber auch mit dem Zugang zu den Entscheidungsdatenbanken von Bundesgerichtshof und Bundespatentgericht hätte man schönen Unfug treiben können. Ärgerlich sind die vielen Webshops (1, 2, 3, 4, 5, 6), bei denen man mit minimalem Aufwand an Daten von Kund*innen kam. Halbwegs interessant waren die Einblicke in die Überwachungsinfrastruktur von Voxsmart und Team Cymru.
Ein Datenleck fehlt und wird bald nachgereicht ‒ wir möchten vor Veröffentlichung noch etwas recherchieren.
Die Datenlecks im Überblick
- Ferrari Academy (env, git)
- Die Partei (Symfony Profiler)
- Emma Matratze (git)
- Plenar TV Niedersachsen (env, phpmyadmin)
- Vevor (Elasticsearch)
- Der Bundesgerichtshof (sqlinj)
- Vino24, Rindchens Weinkontor und Staatsweingut Freiburg (Symfony Profiler)
- LandesSportBund Sachsen-Anhalt (git)
- Acardo (Coupies, Couponplatz, Scondoo) (mysql)
- Voxsmart (Elasticsearch)
- medbill (env, git)
- Prisa (git)
- Fonds Finanz (git)
- Stova / Eventscloud (idor)
- WhiteBIT (Elasticsearch)
- Saatchi & Saatchi (git, phpmyadmin)
- Europäischer Datenschutzbeauftragter (webshell)
- Team Cymru (Elasticsearch)
- GlobalLogic / Meelogic (git)
- Junge Liberale SH (git)
- Philipp Plein (Symfony Profiler)
- Code24 / PiNkey (env)
- Roos Consult / Hamburgs beste Arbeitgeber (git, phpmyadmin)
- Telco-Dinge
- Deutsche Telekom (env, git)
- Lycamobile (git)
- Variatel (env, git)
- TKD Solutions (git)
- Handystar / Mobilezone (git)
- esim.me / TelcoVillage (git)
- WEtell / amiva (Symfony Profiler)
- ReiseSIM / TravelFon (git)
- Berlin (env, git, Symfony Profiler)
Leakvent 25: Berlin
Bis zum 39C3 öffne ich täglich ein Türchen zu den langweiligsten Datenlecks der letzten Jahre. Es geht um .git, .env, exponierte dev-Umgebungen und andere technisch langweilige Ursachen. Aber manchmal ist interessant, was sich hinter einem Türchen verbirgt. Alle Türchen sind hier zu finden.
Auf einem Server unter █.berlin.boanet.de war 2024 ein Symfony Profiler offen zugänglich erreichbar. Dort lagen wie üblich Konfigurationsdaten sowie Zugangsdaten für ein Ticketsystem.
Über das Ticketsystem konnten u.a. gefunden werden:
- EALS-Datensätze mit personenbezogenen Daten (Name, Adresse, E-Mail-Adresse und Handynummer). EALS ist ein Elektronisches Anmelde- und Leitsystem der der Berliner Senatsverwaltung für Bildung, Jugend und Wissenschaft. Es soll Anmeldeprozesse Berliner Schulen vereinfachen und Kommunikation zentralisieren.
- Anmeldungen zur “WiKo” (Name, Telefonnummer, Geburtsdatum, Geburtsland und Staatsangehörigkeit, Sprachstand). WiKo ist die Berliner Willkommensklassendatenbank
- Nextcloud-Shares mit Zertifikaten und zugehörigen private keys (https://cloud.vcat.de/index.php/s/█)
- Weitere Zugangsdaten
Außerdem waren leakende env-Dateien und git-Ordner aufgefallen. Diese sind aber noch nicht alle entfernt worden, daher fehlen hier Details.
Leakvent 24: Telco-Dinge
Bis zum 39C3 öffne ich täglich ein Türchen zu den langweiligsten Datenlecks der letzten Jahre. Es geht um .git, .env, exponierte dev-Umgebungen und andere technisch langweilige Ursachen. Aber manchmal ist interessant, was sich hinter einem Türchen verbirgt. Alle Türchen sind hier zu finden.
Über die letzten Jahre hat sich eine kleine Sammlung technisch langweiliger Datenlecks im Telco-Ökosystem ergeben. Ursache dafür war (oder ist) eine Mischung von .git-Ordnern, .env-Dateien und Symfony Profilern. Belohnt wurde das Stöbern mit Beschäftigtendaten, Sim Inventories, Ausweiskopien und Hotline-Aufzeichnungen.
Deutsche Telekom
Schon Jahre her und relativ wenig Impact hatten drei Lecks bei der Telekom.
Unter https://gard.telekom.de/█/Dashboard.jspa wurde auf einen “GARD Webex Teams Ankündigungs-Chat” verwiesen. Dieser konnte über einen Kurzlink https://eurl.io/#████ betreten werden, auch ohne Telekom-Mitarbeiter zu sein. In dem dazugehörigen Webex-Chat waren Name, Fotos und E-Mail-Adressen von knapp 600 Beschäftigten zu sehen.
Unter https://█.de/.git/config war ein deploy token für gitlab.devops.telekom.de zu finden. Damit konnte aber nur dieses Repository gecloned werden. Der weitere Zugriff über die gitlab-API war eingeschränkt.
[core]
...
[remote "origin"]
url = https://gitlab+deploy-token:██████████
@gitlab.devops.telekom.de/██.git
fetch = +refs/heads/*:refs/remotes/origin/*Bei https://nwkr-intern.telekom.jobs waren dazugehörige env- und env.local-Dateien zu finden. Darin enthalten: API keys, SQL-Zugangsdaten sowie Zugangsdaten für die Webseite.
###> SF CONFIG ###
SFOAPI_USER=██████
SFOAPI_COMPANY=telekom██
SFOAPI_PWD='██████████'
NWKR_INTERNAL_LINK_BASE=https://nwkr-intern.telekom.jobs
SF_SITE_OTE_PLUS_SA=██████████
SF_SITE_GERMANOS_SA=${SF_SITE_OTE_PLUS_SA}
SF_SITE_OTE_AE=${SF_SITE_OTE_PLUS_SA}
SF_SITE_COSMOTE_EVALUE=██████████
SF_SITE_COSMOTE_AE=██████████
...
DATABASE_URL=mysql://telekom:██████████@127.0.0.1:3306/telekom_hr_451
###< doctrine/doctrine-bundle ###Lycamobile
Lycamobile ist ein MVNO, der in fast 20 Ländern aktiv ist und mehr als 15 Millionen Kund*innen versorgt. Unter verschiedenen IP-Adressen waren und sind git-Repositories zugänglich, die offenbar zu Lycamobile gehören.
[core]
...
[remote "origin"]
url = http://newgit.ldinternal.com/lycadev/
newsinglecode-lyca-uk.git
fetch = +refs/heads/*:refs/remotes/origin/*In diesen Repositories gibt es eine Mischung interessanter Dateien,
aus_prod_db.sql, backupspain04-04-18.sql, composer.json, composer.lock, composer.phar, contributing.md, db_spain_new.sql, denmark_db.sql, index.php, license.txt, lyca_gdpr.sql, new_australia_db.sql, new_denmark_db3.sql, new_denmark_db4.sql, readme.rst, smartfocusemail.sql, spain_prod_db.sql, system, uk_prod_db1.sql, uk_prod_db2.sql, uk_prod_db.sql,
und git branches:
ADD_SFMC_IN_UK_STAGE, lmde-postpaid-platform, master, plat-prod-de, 2Oprod, 2oApisGERPROD, 2oSpain, 2oUKPROD, 2oapiProd, 2oprodmove, ADD_ESIM_IN_GERMANY_PROD, FreeSimGermStage, UK_LATEST_STAGE, UK_NEW_ENTITY_FOR_MOBILE, UK_PLATFORM_LATEST_STAGE, UKstage_ipaddress, Uk_loyalty_changes, ValidationPROD, add-fields-rates, add_organization_name, de-preprod-mobile, de_platform, delete_api, lycaprod_germany.
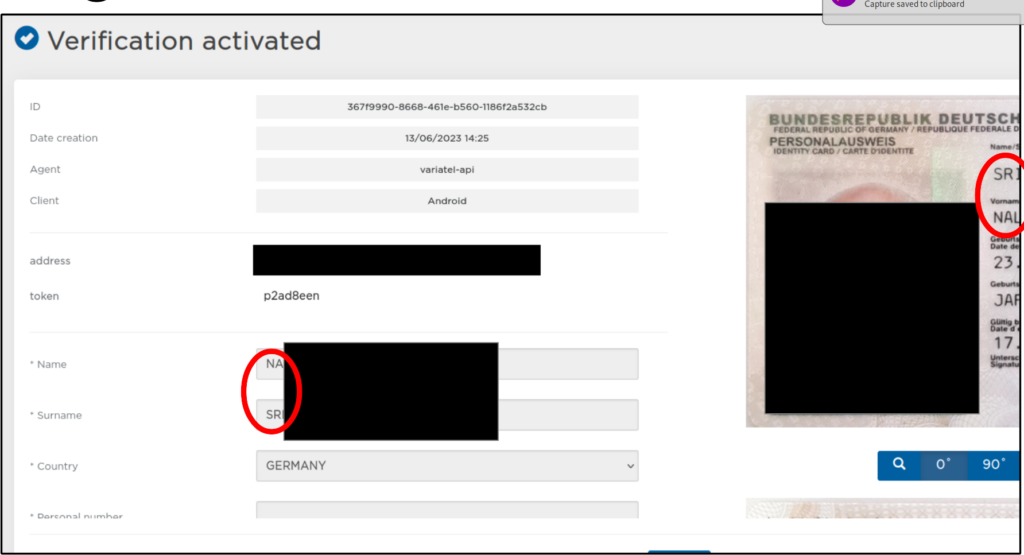
Eine der Dateien enthielt einen gültigen API key für Complycube, einem Dienst für KYC und identity verification. Damit konnte u.a. auf Bilder von Ausweisen zugegriffen werden.

Auf diverse Nachrichten über verschiedene Kanäle hat Lycamobile bisher nicht angemessen reagiert. Wer sucht, findet leicht weitere git-Repositories.
Variatel
Variatel ist ein MVNO, deutlich kleiner als Lycamobile und nur in Deutschland tätig, im Netz der Deutschen Telekom. Unter http://█.█.█.█/.env leakte im März/April 2023 eine env-Datei. Diese Datei enthielt Zugangsdaten für einen Datenbank-Server:
DB_CONNECTION=pgsql
DB_HOST=127.0.0.1
DB_PORT=5432
DB_DATABASE=variateldb
DB_USERNAME=████████
DB_PASSWORD=████████Dieser Datenbank-Server war unter stagebkend.variatel.de im Internet zu erreichen. Die gleichen Zugangsdaten wurden im Produktivsystem unter ec2-█.eu-central-1.compute.amazonaws.com genutzt. Auch dieser Datenbank-Server war einfach so zu erreichen.
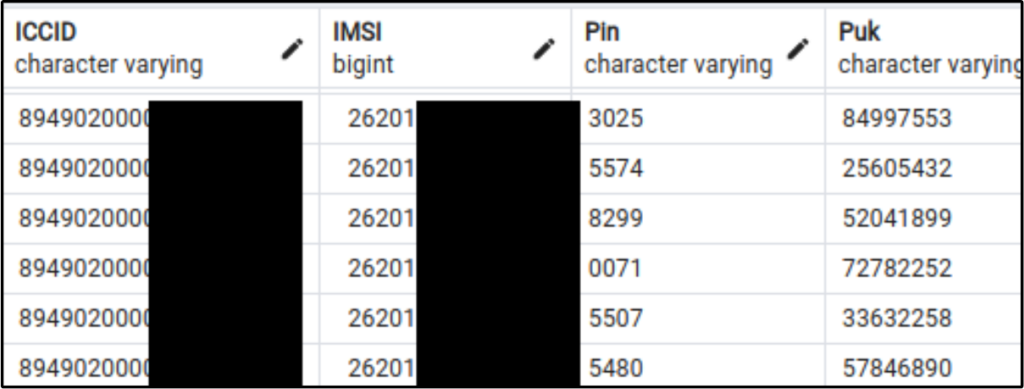
Über diesen Zugang konnte mittels pg_read_file eine aktuellere env-Datei ausgelesen werden. Diese enthielt einen gültigen API key für mobbeel, einem Dienst für KYC und identity verification.
MOBB_SCAN_AGENT_URL=https://mobbscan-cloud.mobbeel.com/mobbscan-agent
ALTEN_API_USERNAME=variatel-api
ALTEN_API_PASSWORD=████████Damit konnte u.a. auf Bilder von Ausweisen aus ca. 13.000 Verifizierungsvorgängen zugegriffen werden.
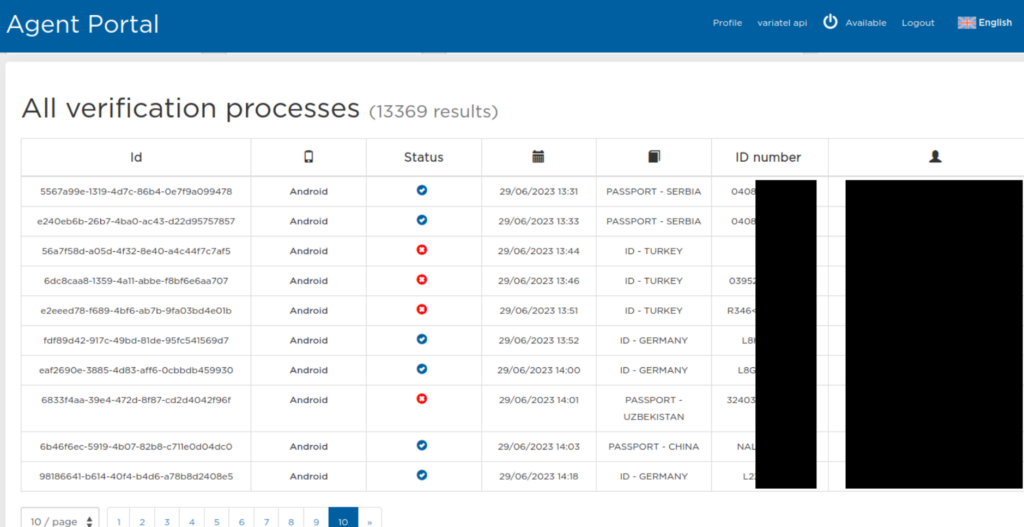
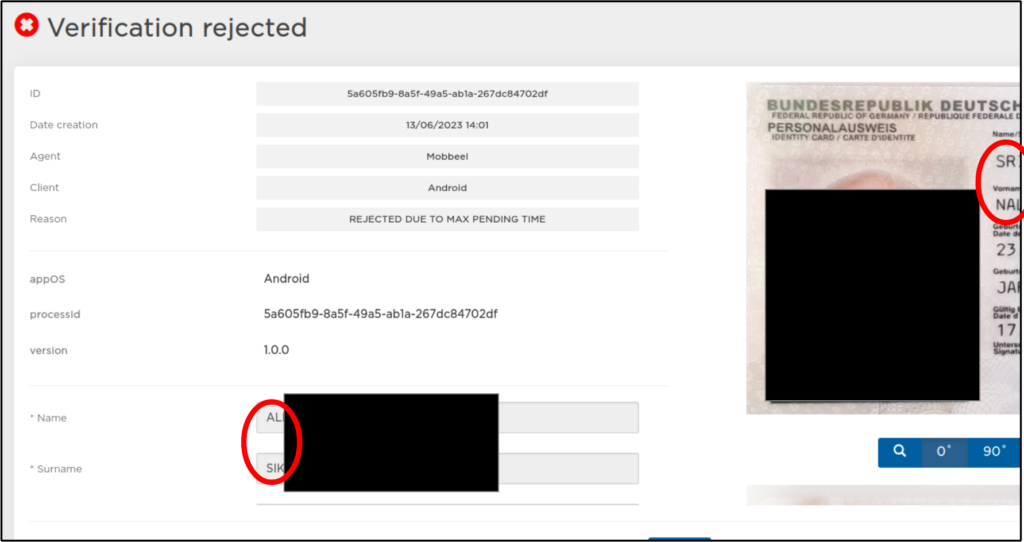
Außerdem konnte auf Call Data Records zugegriffen werden.
SFTP_HOST=██.██.██.██
SFTP_USERNAME=████████
SFTP_PASSWORD=████████
SFTP_PRIVATE_KEY=████████
Weiterhin gab es eine Datenbank readme_to_recover mit einem Hinweis darauf, dass Daten von dem Server kopiert wurden.
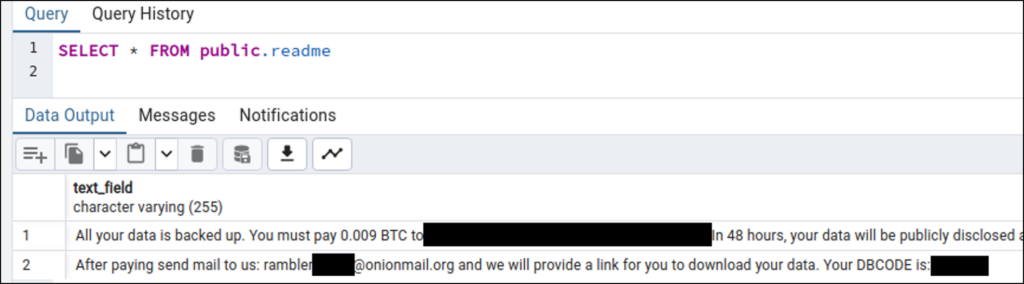
Auf mehrere Meldungen hat Variatel nicht geantwortet. Unter http://stagebkend.variatel.de/.git/ wird der Quellcode der Anwendung weiterhin zur Verfügung gestellt.
[remote "origin"]
url = https://github.com/cognitude-dev/variatel-be.git
fetch = +refs/heads/*:refs/remotes/origin/*TKD Solutions
TKD bietet Device as a Service an. Auch hier war 2024 ein git-Repository abrufbar.
[core]
...
[remote "origin"]
url = https://██████████████@dev.azure.com/TKDSolutions/
████Auftragsliste
fetch = +refs/heads/*:refs/remotes/origin/*Ein Skript war anfällig für eine SQL-Injection. Passwörter wurden mit dem veralteten Hashverfahren md5 und ohne Salt gespeichert. Sie bestanden oft aus dem ersten Buchstaben des Vornamens und dem Nachnamen.
Diese Zugangsdaten erlaubten den Zugriff auf ein Portal zur Auftragserfassung, ein zweiter Faktor wurde beim Login nicht verlangt. In dem Portal konnten u.a. Stammdaten von Nutzer*innen und Kund*innen, Rufnummern und SIM-Seriennummern eingesehen werden.
Handystar / Mobilezone
Mobilezone betreibt den Teleshopping-Sender Handystar. Auch hier war 2024 ein git-Repository abrufbar.
[init]
...
[core]
...
[remote "origin"]
url = https://gitlab-ci-token:████████████
@gitlab.com/████/abwicklungssystem.git
fetch = +refs/heads/*:refs/remotes/origin/*Ein Skript war anfällig für eine SQL-Injection. Passwörter wurden mit dem veralteten Hashverfahren md5 und ohne Salt gespeichert. Das Passwort eines Nutzers konnte in wenigen Sekunden wiederhergestellt werden.
Diese Zugangsdaten erlaubten den Zugriff auf ein Portal zur Bestellabwicklung, ein zweiter Faktor wurde beim Login nicht verlangt. In dem Portal konnten u.a. Stammdaten von Kund*innen eingesehen und Aufzeichnungen der Bestell-Hotline abgehört werden.
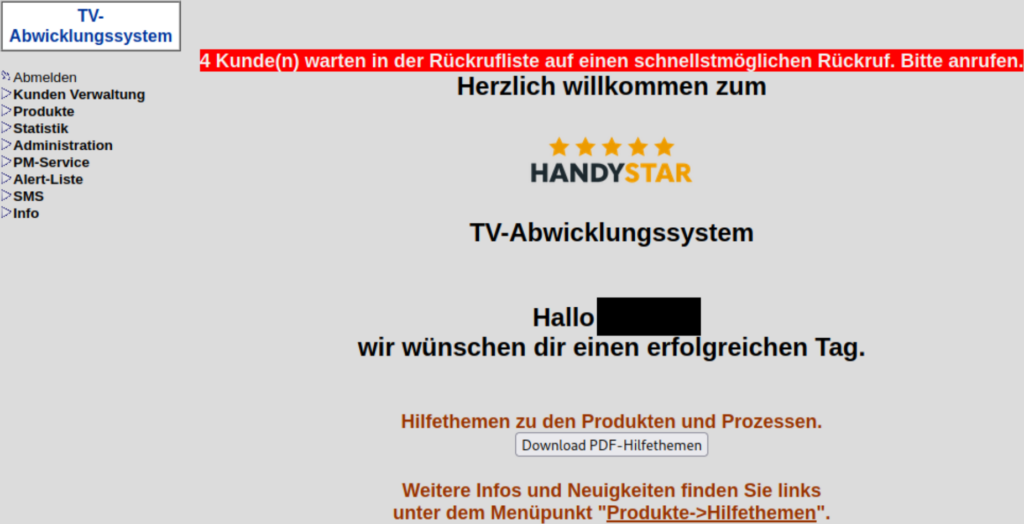
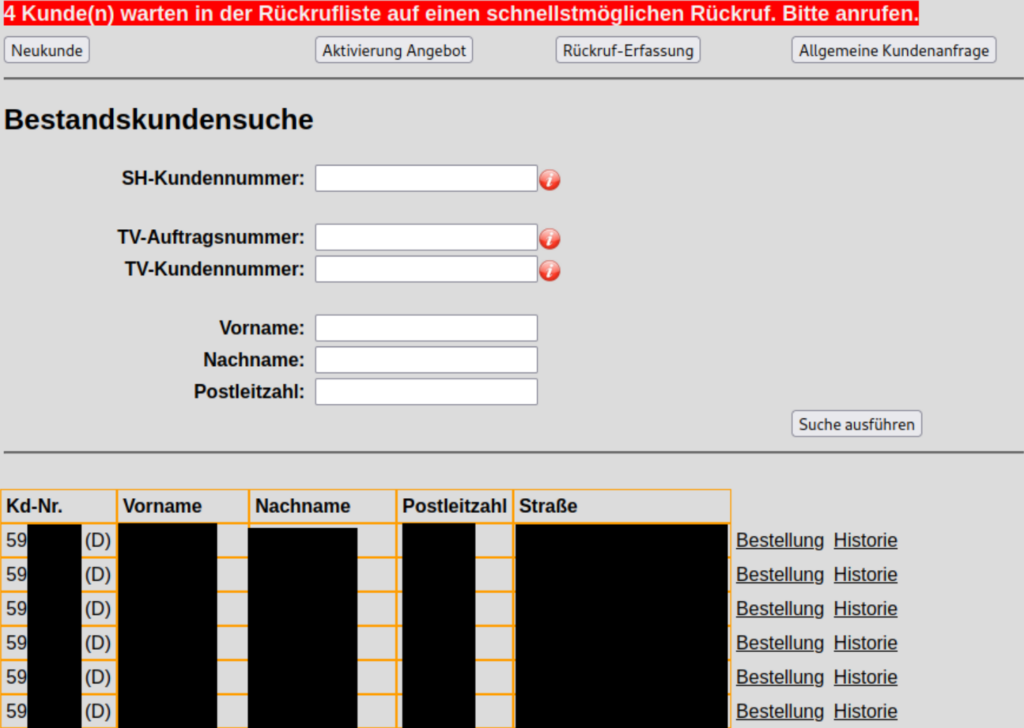
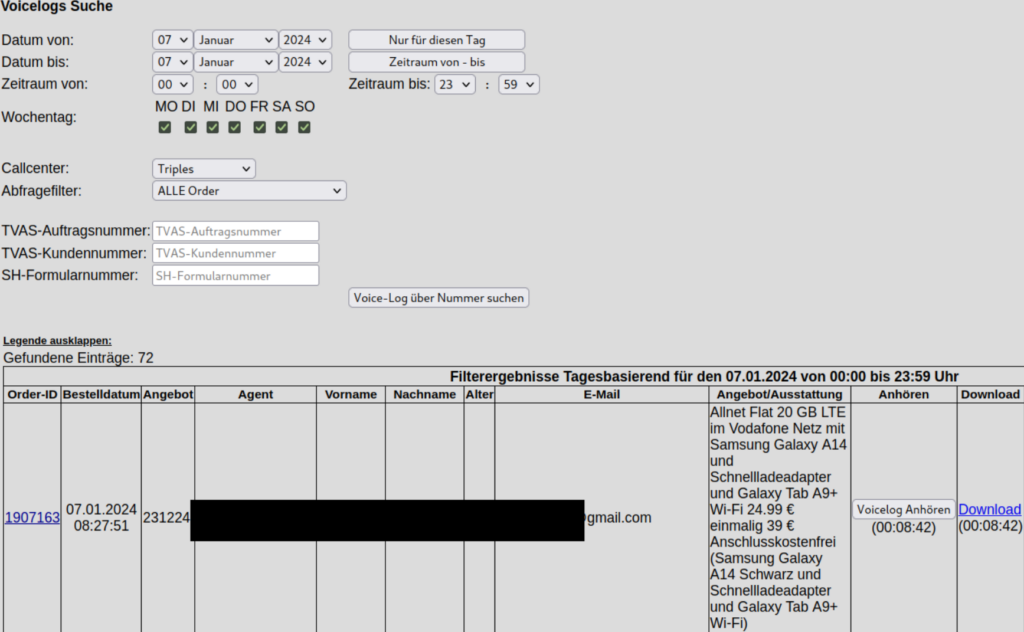
Das Unternehmen beauftragte eine größere Kanzlei zu prüfen, ob Betroffene benachrichtigt werden müssen: “Eine Benachrichtigung der betroffenen Personen gem. Art. 34 DSGVO ist nach unserer Auffassung nicht erforderlich.”
esim.me / TelcoVillage
TelcoVillage vertreibt unter anderen “Hardware-eSIMs” ‒ SIM-Karten, die ältere Geräte eSIM-fähig machen. Auch hier war 2025 ein git-Repository abrufbar.
[core]
...
[remote "origin"]
url = https://██@bitbucket.telcovillage.com/██.git
fetch = +refs/heads/*:refs/remotes/origin/*In dem Repository waren viele php-Dateien zu finden,
… index03052018.php, index0.php, index1.php, index20171031.php, index20180122.php, index2.php, index_ajax.php, indexBkp.php, indexGD.php, index_good_22052018.php, indexGood.php, index_no_ajax.php, index.php, …
Manche der Dateien enthielten gültige root-SSH-Zugänge.
<?php
...
if (!($resource=@ssh2_connect("█.█.█.█",22))) {
echo "[FAILED]<br />";
exit(1);
}
...
if (!@ssh2_auth_password($resource,"root","█████████████")) {
echo "[FAILED]<br />";
exit(1);
}
...Das ging unerwartet schnell.
WEtell / amiva
Unter https://teststage.wetell.de/_profiler/ war 2024 ein Symfony Profiler offen zugänglich erreichbar. Über diesen konnten u.a. Formulareingaben mit Zugangsdaten im Klartext sowie Konfigurationsdaten eingesehen werden.
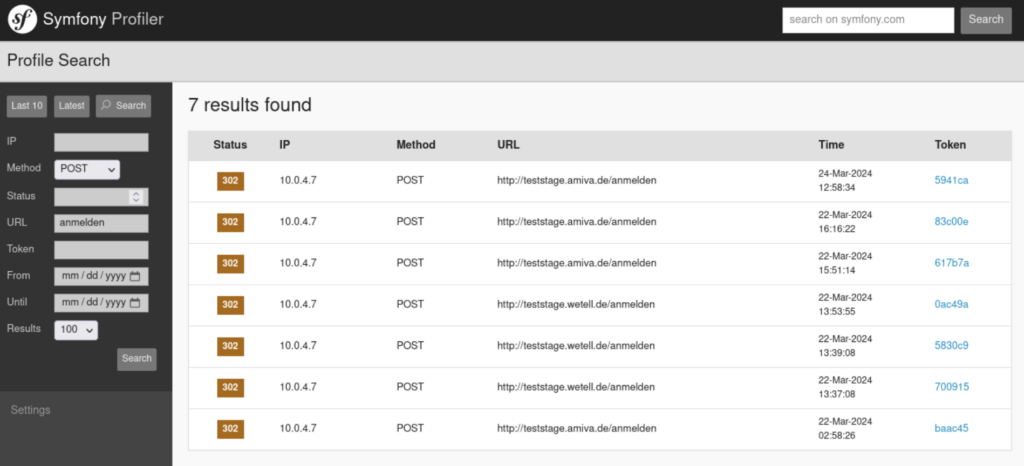
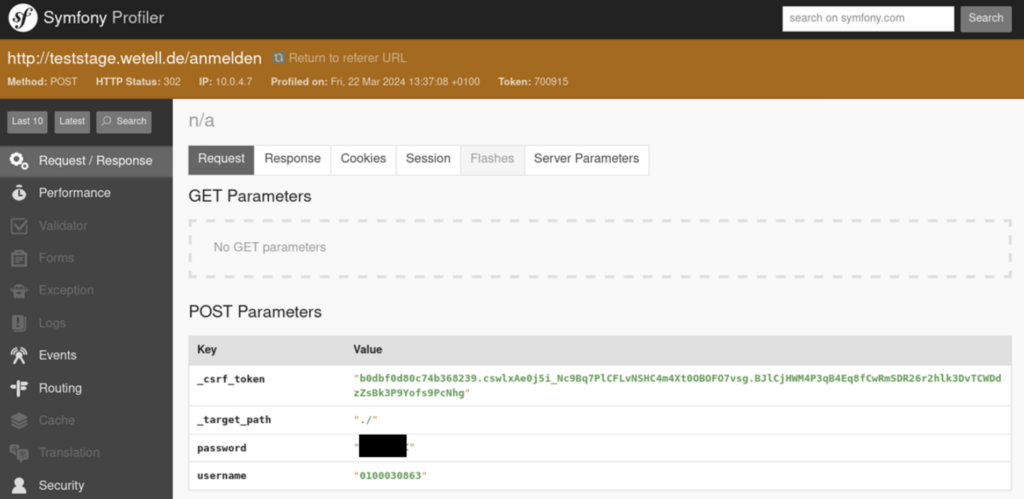
Diese Zugangsdaten erlaubten den nicht-administrativen Zugriff auf die Portale http://teststage.wetell.de/ bzw. http://teststage.amiva.de/.
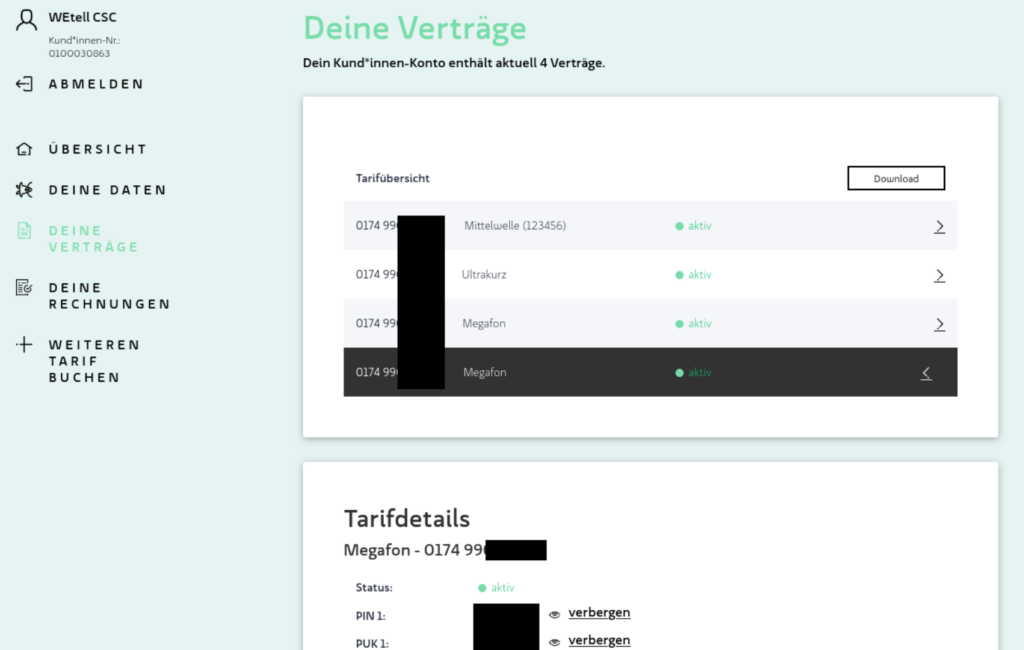
ReiseSIM / TravelFon
TravelFon vertreibt unter ReiseSIM SIM-Karten und eSIMs. Auch hier war 2025 ein git-Repository abrufbar.
[core]
...
[remote "origin"]
url = ssh://gogs@gitlab.travelfon.eu██/██reisesim.de.git
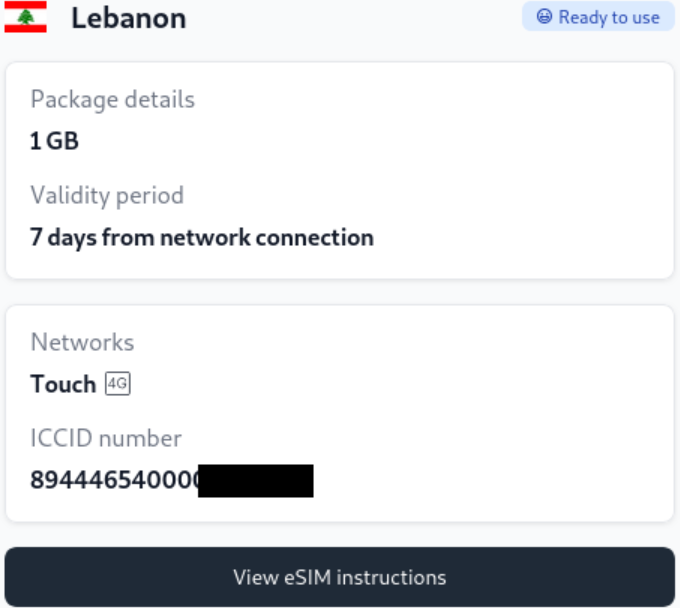
fetch = +refs/heads/*:refs/remotes/origin/*In dem Repository waren viele php-Dateien zu finden. Eine der Dateien enthielt gültige Zugangsdaten für eine Airalo-API. Airalo ist ein großer eSIM-Händler. Damit konnten u.a. vergangene eSIM-Bestellungen einschließlich QR-Code abgerufen werden.
<?php
…
$clientid = '537███████████████';
$clientsecret = '███████████’;
$api = 'https://partners-api.airalo.com/’;
$accesstoken = '█████████████████’;
…
Leavent 23: Roos Consult / Hamburgs Beste Arbeitgeber
Bis zum 39C3 öffne ich täglich ein Türchen zu den langweiligsten Datenlecks der letzten Jahre. Es geht um .git, .env, exponierte dev-Umgebungen und andere technisch langweilige Ursachen. Aber manchmal ist interessant, was sich hinter einem Türchen verbirgt. Alle Türchen sind hier zu finden.
Roos Consult zeichnet “Hamburgs beste Arbeitgeber” aus. Dazu werden Mitarbeitende befragt. Die Teilnahme soll anonym möglich sein. In der Datenschutzerklärung heißt es:
Die Befragung erfolgt anonym, d.h. einzelnen Antworten können keine konkreten Personen zugeordnet werden.
Wir sichern Ihnen zu, dass selbstverständlich Ihre Anonymität gewährleistet ist. Nach Registrierung der Antworten werden diese umgehend elektronisch erfasst, verarbeitet und weiter anonymisiert. Nach Abschluss der Untersuchungen werden die Daten gelöscht.
Möglicherweise war die Befragung dann aber weniger anonym.
- Unter https://self-bf.de/.git/ lag 2024 Quellcode.
- Das Skript
core/funcs.phpenthielt Datenbank-Zugangsdaten:
$servername = "localhost";
$username = "██████";
$password = "███████████████████████████";
$dbname = "██████";- Über ein PhpMyAdmin unter http://█.█.█.█/phpmyadmin/ konnte auf die Datenbank zugegriffen werden.
Dort konnten dann die Antworten befragter Personen, deren TANs oder an diese versandte E-Mails sowie Passwörter, z.T. im Klartext, von Admin-Accounts eingesehen werden.



Leakvent 22: Code24 / PiNkey AG
Bis zum 39C3 öffne ich täglich ein Türchen zu den langweiligsten Datenlecks der letzten Jahre. Es geht um .git, .env, exponierte dev-Umgebungen und andere technisch langweilige Ursachen. Aber manchmal ist interessant, was sich hinter einem Türchen verbirgt. Alle Türchen sind hier zu finden.
Code24 ist ein Dienst, der die Rückgabe verlorener Gegenstände ermöglichen soll. Gegenstände müssen mit einem individuellen Code markiert werden. Wird ein markierter Gegenstand gefunden, kann die Eigentümerin per SMS oder E-Mail benachrichtigt werden.
Das funktioniert aber nur, wenn rechtzeitig bezahlt wird, denn bezahlt wird dieser Dienst für ein oder mehrere Jahre im Voraus. Ist die Laufzeit abgelaufen, können (oder wollen) Fundmeldungen nicht mehr weitergeleitet werden.
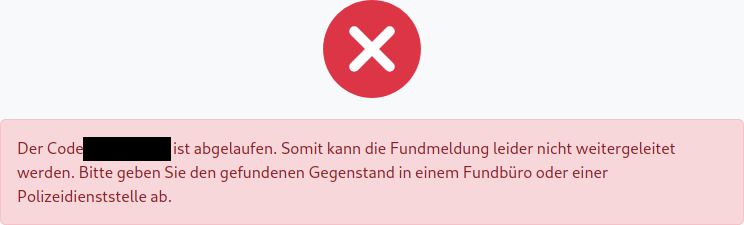
Seit mehr als drei Jahren liegt bei Code24 eine env-Datei mit Umgebungsvariablen herum. Das Leck wurde mehrfach gemeldet, auch beim Thüringischen Datenschutz. Seither wurden die Zugangsdaten wenigstens einmal rotiert. Die env-Datei liegt aber weiterhin herum und mit älteren Zugangsdaten kann auch noch immer auf eine Datenbank mit Codes und Daten von Kund*innen zugegriffen werden.
Leakvent 21: Philipp Plein
Bis zum 39C3 öffne ich täglich ein Türchen zu den langweiligsten Datenlecks der letzten Jahre. Es geht um .git, .env, exponierte dev-Umgebungen und andere technisch langweilige Ursachen. Aber manchmal ist interessant, was sich hinter einem Türchen verbirgt. Alle Türchen sind hier zu finden.
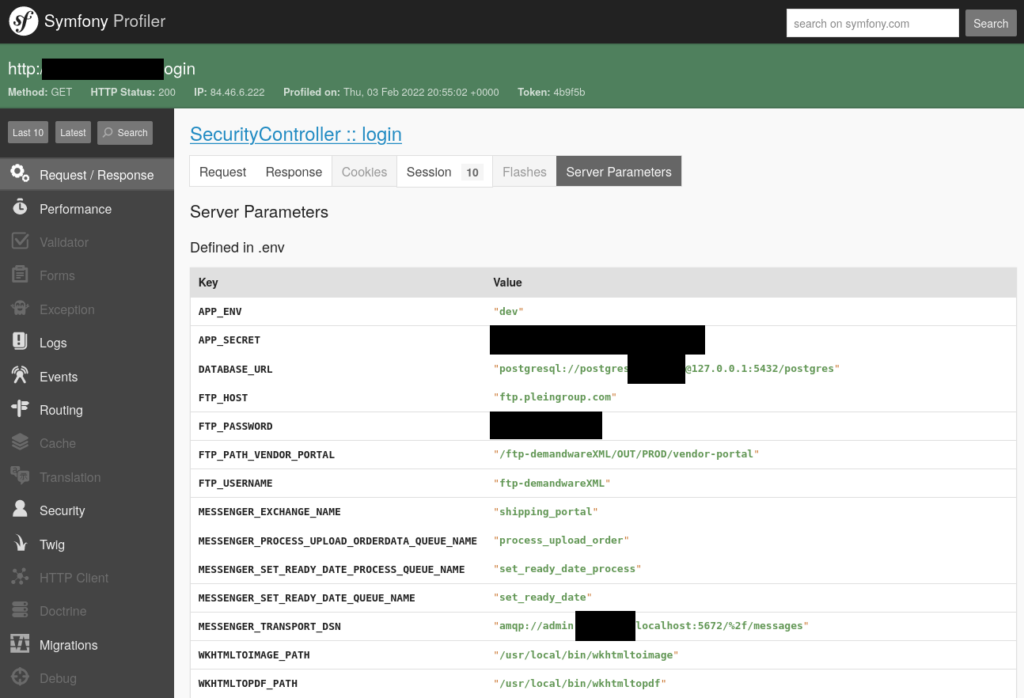
Bereits 2021 war beim Crypto King Philipp Plein ein Symfony Profiler für alle zugänglich im Netz. Ich rief dort an, schrieb E-Mails, kontaktierte den Chief Digital Officer via Linkedin, meldete mich beim GovCERT in der Schweiz und bei der Berliner Datenschutzbehörde ‒ lange passierte nichts. Erst 2022 oder später verschwand der Profiler aus dem Internet.
Über den Profiler konnten frühere Formulareingaben eingesehen werden, zum Beispiel Zugangsdaten für ein Shipping Portal.
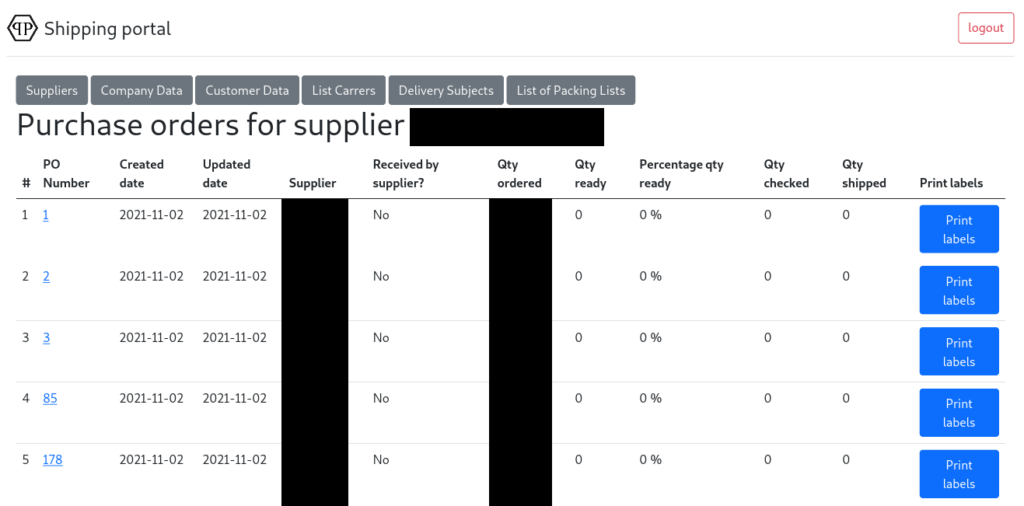
Das sah relativ langweilig aus. Aber der Profiler spuckte auch gültige Zugangsdaten für ftp.pleingroup.com aus.
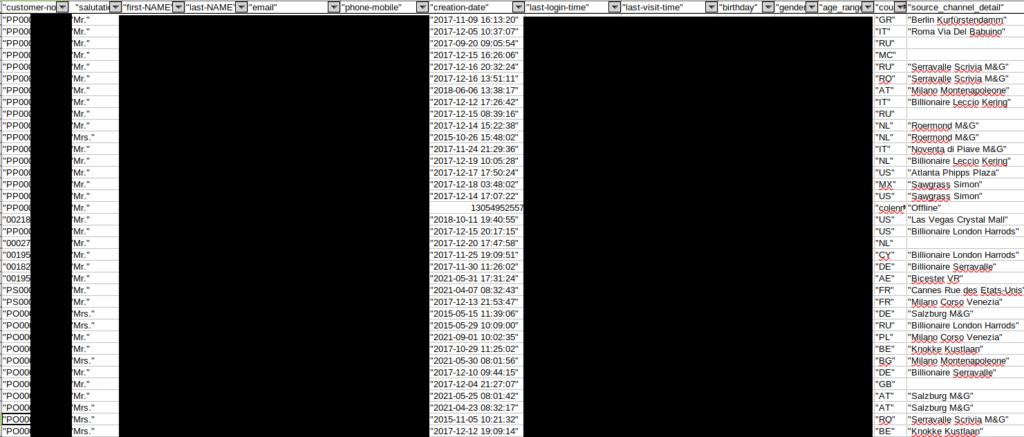
Unter /ftp-demandwareXML/CRM/transaction_address/archive/ befanden sich allein in der Datei transactions_address_20210921.csv fast 800.000 Datensätze mit Namen, Adresse, E-Mail-Adresse, Geschlecht und Telefonnummer. Andere Dateien enthielten auch Geburtsdaten. Es wurden regelmäßig neue Daten geliefert und es gab auch Bilder von Reklamationen zu sehen.
Das war erst einmal nicht ungewöhnlich. Exponierte Symfony Profiler führen häufig zu Daten von Webshop-Kund*innen. In diesem Fall war jedoch besonders, dass auch frische Daten aus Filialen der Modefirma zugänglich waren, z.B. der Filiale im Kurfürstendamm. Aus diesem Grund wurde das Leck auch an die Berliner Datenschutzbehörde gemeldet.
Auf keinen der zahlreichen Kontaktversuche hat Plein sich zurückgemeldet.
Leakvent 20: Junge Liberale SH
Bis zum 39C3 öffne ich täglich ein Türchen zu den langweiligsten Datenlecks der letzten Jahre. Es geht um .git, .env, exponierte dev-Umgebungen und andere technisch langweilige Ursachen. Aber manchmal ist interessant, was sich hinter einem Türchen verbirgt. Alle Türchen sind hier zu finden.
Bei den Jungen Liberalen Schleswig-Holstein, bekannt durch radikale Forderungen wie “Freies Parken für freie Bürger“, war 2023 ein git-Repository offen zugänglich. Dieses enthielt neben Quellcode auch einen Schlüssel im Klartext. Mit diesem konnte unter https://lako.julis-sh.de/export.php?token=█ auf Namen und E-Mail-Adressen der Teilnehmenden eines Landeskongresses zugegriffen werden.